Five Elements of a Cyber-Secure BYOD Policy
Between 80 and 90 percent of the U.S. workforce prefers to work from home at least some of the time, according to GlobalWorkplaceAnalytics.com. The modern workforce craves flexibility, and the technology needed to provide it is more readily available than ever before.
However, small and medium-sized businesses (SMBs) can’t necessarily afford to give their entire workforce laptops, tablets and smartphones to facilitate working remotely or while on the go. Instead, many SMBs have implemented bring-your-own-device (BYOD) policies that let employees get work done on their personal devices. Offering this option can actually be a competitive advantage, and not just for the work-from-home benefits. Employees can bring a laptop into the office, for example, that they feel more comfortable working on.
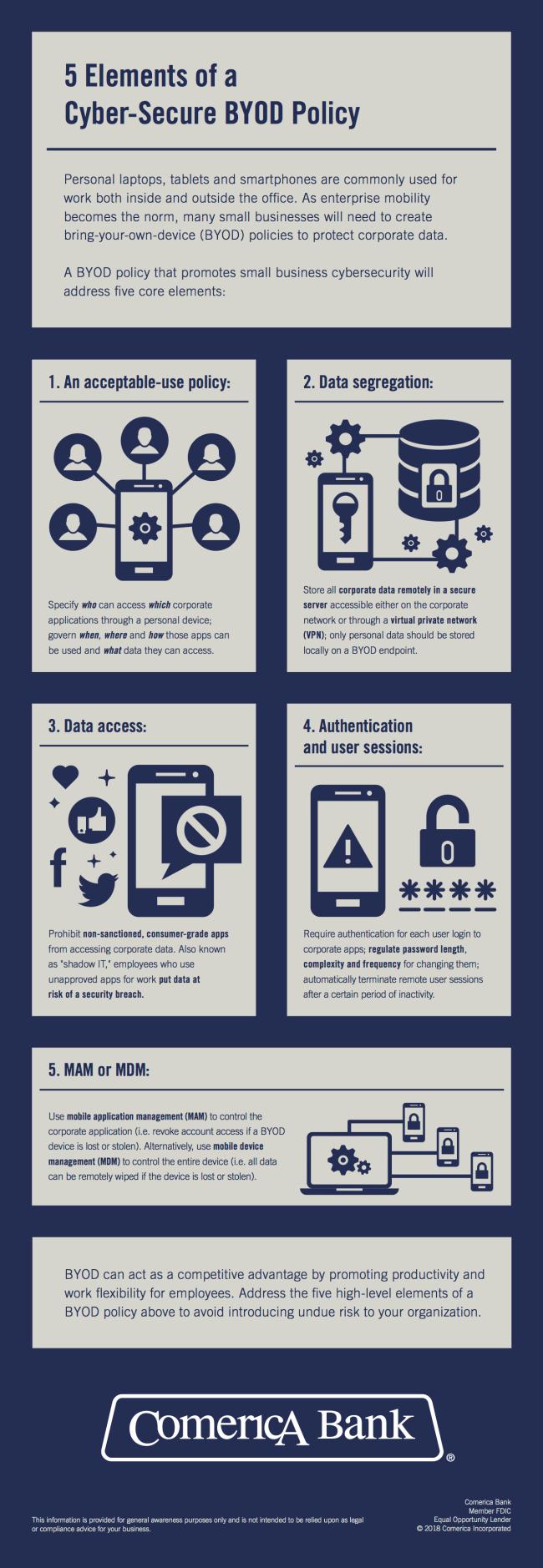
For a BYOD policy to be successful, it must make small business cybersecurity a priority. This means that employers need to establish security measures that protect corporate data. If, for example, a lost or stolen tablet or smartphone ends up in the wrong hands, the result could be a damaging data breach. How will your organization respond to this incident? Will it implement mobile device management (MDM) systems so that smartphones can be remotely wiped? These are the types of questions a small business must address as part of implementing a BYOD policy.
From keeping personal data and company data separate, to establishing an acceptable-use policy, to requiring user authentication and more, SMBs need to create a cyber-secure BYOD policy. This is key to protecting digital assets while empowering employees.
We discuss the fundamental components of a BYOD policy in more depth in the following “5 Elements of a Cyber-Secure BYOD Policy” infographic.












